AND ESCAPING PROSECUTION?
by Sharon Rondeau
 (Nov. 2, 2017) — For the last 15 months, an advocate working with the power of attorney (POA) of a U.S. Army soldier whose story The Post & Email began covering in June of last year has reported a myriad of cyber-crimes and stalking to his local police department, local FBI office, and equipment technicians, the latter of whom have confirmed that intrusions and disabling have taken place.
(Nov. 2, 2017) — For the last 15 months, an advocate working with the power of attorney (POA) of a U.S. Army soldier whose story The Post & Email began covering in June of last year has reported a myriad of cyber-crimes and stalking to his local police department, local FBI office, and equipment technicians, the latter of whom have confirmed that intrusions and disabling have taken place.
The soldier, who in 2012 alleged that he witnessed egregious misconduct on the part of several in his chain of command while stationed in South Korea, is now disabled and was discharged in early January of this year.
In July 2016, the POA told The Post & Email that her Yahoo! email account was hacked, with the perpetrator appearing to be a member of the soldier’s chain of command based on an email she received. “In July of last year XXXXX hacked me with an email that required verification,” the POA said.
Two months later, the POA told The Post & Email, “After I was hacked, all of my contacts who are advocates for the soldier were hacked as well. When they hacked my email, they were able to see who I was sending email to, including [second soldier advocate]. So they sent him an email as if it was from his cousin, and when he opened the email, there was a link with a virus which went through everything he had. They interrupted his internet service and cut off all his communication.”
The POA told The Post & Email that a new phone she purchased was mysteriously disabled after her email account was breached. “This was a brand new phone. I had to take it back to the store and get it reset to factory! That’s how I knew it was hacked,” she said, adding that the laptop she was using for her job was also affected.
 Both the POA and the Hawaii advocate told The Post & Email that USPS mail between them has not arrived at either destination for more than a year.
Both the POA and the Hawaii advocate told The Post & Email that USPS mail between them has not arrived at either destination for more than a year.
The POA contacted the FBI about the hacking she experienced. In addition to telephone and computer breaches, on March 18 of this year, she described to this publication “extensive surveillance by people in SUVs with darkly-tinted windows parked outside of her home for months and strange phone calls from unrecognizable numbers.”
A third advocate, who was also the soldier’s spiritual adviser, reportedly received “weird phone calls.” He reported receiving what he perceived to be a death threat via email, a claim he reiterated in an interview with The Post & Email on October 17.
In addition to hacking, physical stalking, and phone calls from strange phone numbers and unknown parties, the POA reported early this year that an electronic bank-account breach resulting in the theft of more than $50,000 from the soldier was acknowledged and rectified by Navy Federal Credit Union (NFCU).
The Hawaii advocate reported that he believes the U.S. military is the perpetrator of the computer and telephone interference in retaliation for the assistance he rendered to the POA on the soldier’s behalf. Late last summer, he told us:
To stop my communication with XXXXXXX and XXXXXXX, since early August I’ve been targeted by the military with a level of cybercrime at the level of an enemy state attack. Four of my computers have been compromised and rendered unusable by writing remote access code to their memory chips. No matter what time of day or night, cyber criminals would take over the computers whenever I would log on, then scramble or block any attempts I made to access the Internet. They infected backups and other information on 4 of my external drives,” he told us for our September 5, 2016 report.
When I went to XXXX to attempt access, they shut down two local networks there rendering them useless for the weekend. When I go to my local library, Starbucks, or McDonald’s, they were there too, blocking my access by locking out wi-fi. I strongly suspect tracking and listening devices have been placed somewhere in my vehicles and adjacent to my home because they always are waiting where ever I go and know details of my plans.
In an interview on October 16, the Hawaii advocate told The Post & Email that the cyber-attacks and intrusions into his equipment have continued unabated, disabling considerably more equipment and incurring over $100,000 in repair costs and small-business losses since it began.
He has filed a total of two dozen criminal complaints with the Honolulu Police Department (HPD), many of which The Post & Email has reviewed. In response to 911 calls made by the Hawaii advocate as directed by HPD, police officers visited his home office, observed the compromised computers at his request, and included their findings in their respective police reports.
In yet another aspect of the intrusions he has experienced, the advocate told us, “In October 2017 I scanned my vehicle with a professional-grade ‘bug’ detector costing several hundred dollars. The device confirmed tracking bugs were installed in my vehicles, as the detector lit up like a Christmas tree.”
 The advocate visited the Kapolei office of the FBI on five occasions. On three of the visits, he delivered detailed reports explaining the crimes to an FBI desk officer. At each visit he requested a cybercrime agent but was told none were available.
The advocate visited the Kapolei office of the FBI on five occasions. On three of the visits, he delivered detailed reports explaining the crimes to an FBI desk officer. At each visit he requested a cybercrime agent but was told none were available.
In 2016, the advocate wrote two letters two months apart to the FBI detailing what he described as “dire” circumstances and asking for assistance in locating and apprehending the cyber-predators. He also filed two complaints through the FBI’s IC3 cyber-crime web portal which he shared with this publication. None of his submissions were answered.
“The surveillance has been extraordinary. Every facet of my life has been monitored. Before I knew what was going on, my phone was used to connect to the other computers to disable them, but they would also have on a phone camera. In everything my wife and I did, they were watching us. That’s the demonic part of this. This has gone on hourly, daily and weekly for 15 months. The purpose of this is to keep everything that happened silent by keeping me off the Internet. If I or the others can be knocked offline, no one will know. My assumption was that once the soldier was discharged, this would stop, but that is not the case,” he told us.
On Thursday, October 19, 2017, The Post & Email spoke with Det. Choi, who informed us that the case exceeded the HPD’s capabilities and that he therefore referred it to the FBI.
The Post & Email has submitted a request under Hawaii’s UIPA, or open records law, for a copy of Choi’s referral to the FBI. A second FOIA request has been electronically submitted to the FBI for all documents it might possess relating to the advocate’s complaints of cyber-stalking, disabling of his equipment, and the “bugging” of his personal vehicle.
An article published earlier this month at thehackernews.com reported that the FBI has the forensic tools to identify cyber-criminals.
Excerpts from the Hawaii advocate’s reports to the HPD include:






“Three weeks ago my Apple desktop, with its Wi‑Fi and Bluetooth connections disabled to prevent rogue connections, was attacked and infected through its only remaining connection to a wired printer,” the Hawaii advocate told The Post & Email on Monday in an update.
Hawaii has specific laws aimed at locating and prosecuting those perpetrating cyber-crimes. On October 20, 2017, The Post & Email spoke with Chris Duque, a retired HPD detective with extensive experience in forensic analysis. Having joined the office of the prosecuting attorney for the City and County of Honolulu in 2013, Duque serves as an investigator who sees that all of the necessary information from law enforcement is compiled for the prosecutor’s review on any given case.
Duque said he receives between “a half-dozen to a dozen calls a day,” although not all result in prosecution. “At the prosecutor’s office, they won’t initiate a case per se,” he said, and that upon receipt of a complaint, he always asks if the complainant first filed a report with the HPD or the FBI.
A 27-year disabled military veteran, the Hawaii advocate is convinced that the techniques and abilities exhibited by the cyber-stalkers are not available to the average hacker, but rather, only to the federal government, an assessment with which Duque agreed during our interview.
In recalling the advocate’s specific case, Duque said that if the perpetrators are embedded within the federal government and/or U.S. military, it is “beyond my pay grade” and the U.S. Justice Department would be the agency to handle the complaints.
Regarding his reports to local law enforcement, Duque and the FBI, the Hawaii advocate told The Post & Email:
In addition to my technicians validating the hacks, HPD officers who responded to my 911 calls observed compromises on my computers and phones. In many cases I walked them through onscreen what happened, or showed them the end result of the damage. I ensured the viewings of my compromised hardware and software was analogous to what they would see if the damage was on their property. Each officer who received my showings validated what they observed in their reports. I wasn’t able to deliver the visuals in every case, but for those I did, the evidence was compelling enough to merit opening and
One of my main issues with the FBI is their not acting on the HPD report Det. Choi states he submitted. FBI doctrine states they require local law enforcement to validate a crime before getting involved.
Various Apple technical reports confirm that the Hawaii advocate’s equipment has been damaged extensively and repeatedly over a long period of time. A report from a technician at his licensed Apple retailer dated December 6, 2016 reads:
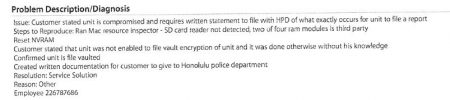
A subsequent visit to the same company on January 4, 2017 regarding two IPhones yielded the following technical findings:

On February 21, 2017, the Hawaii advocate again visited the Apple dealer for troubleshooting and repair of a computer. The finding of the technician was that the computer would not allow the user to progress past the Apple logo screen, rendering it “inoperative.”

A service report dated August 22, 2017 on a computer indicates that foreign “networks” were found and removed by the technician.


